Business LOG
Thousands of organizations (small, medium and large companies) have already chosen Business LOG as their Log Management Suite for IT system security and corporate compliance (compliance NIS2, GDPR, ISO 27001 and Privacy Policy regarding the role of the System Administrator).


Stay compliant and leverage the Business LOG monitoring capabilities within your organization
GDPR compliance — Regulatory compliance
ISO 27001 compliance — Regulatory compliance
Compliance with the regulations concerning System Administrators — Regulatory compliance
NIS2 compliance — Regulatory compliance
Regulatory compliance.
Business LOG is a platform that helps companies comply with data management and retention regulations, such as GDPR, ISO 27001 and NIS2, providing a secure and centralized system for managing company logs.
Using advanced encryption techniques and access controls, it ensures the collection, storage and secure management of data, reducing the risk of penalties for regulatory violations and improving stakeholder confidence.
Operational efficiency.
Business LOG significantly improves the operational efficiency of organizations.
By automating log collection and analysis, the platform reduces the manual workload of IT staff, freeing up resources for other critical tasks.
The platform provides advanced reporting and visualization tools, facilitating the identification of trends and recurring problems, thus enabling timely and targeted interventions.
In-depth analysis.
The platform continuously analyzes log data, allowing companies to detect anomalies and security threats that could compromise systems.
With detailed reports and real-time alerts, IT can take action in a timely manner, reducing downtime and improving security.
This proactive monitoring ensures regulatory compliance and strengthens resilience against cyber attacks.
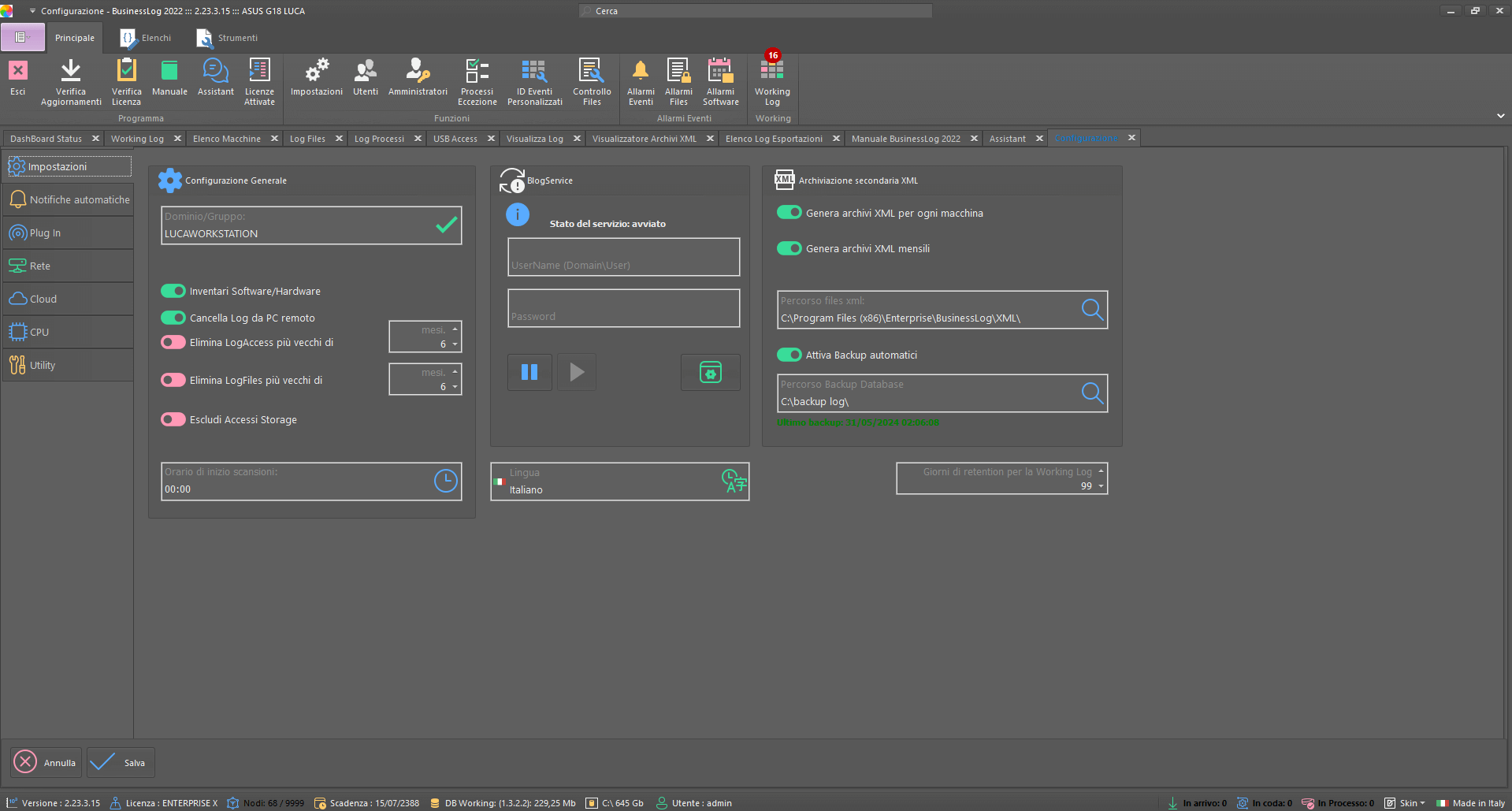
Setup wizard
Getting started with Business LOG is quick and easy thanks to the initial setup that allows you to easily install the software and manage your main Business LOG configurations.
Custom alarms
One or more alarms can be established in Business LOG to be triggered when an event occurs on custom files, folders, software, or events defined directly by the user.
When the desired alarm occurs, you can preset a command via Power Shell and/or notify a specific email about the alarm detected.
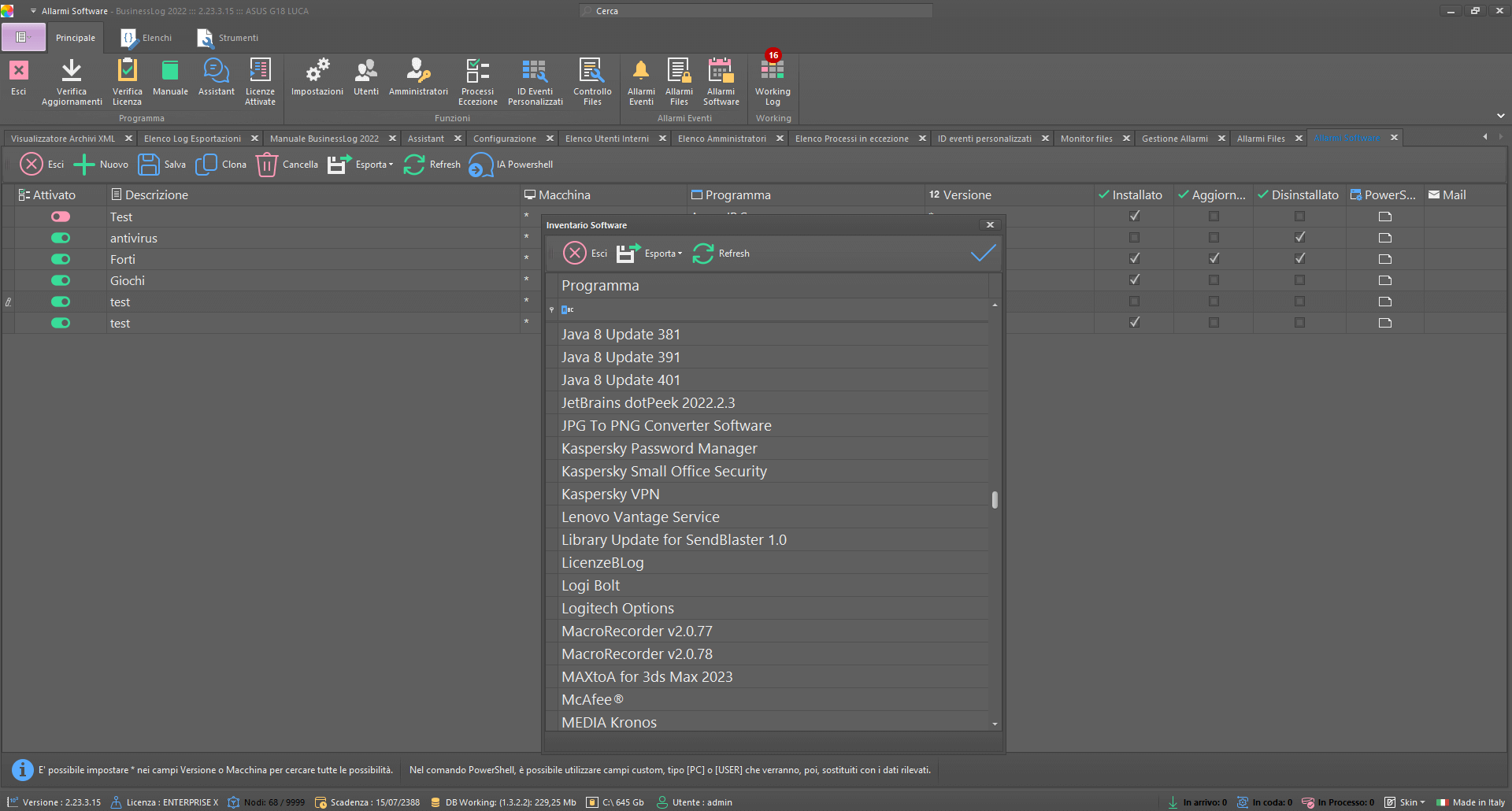
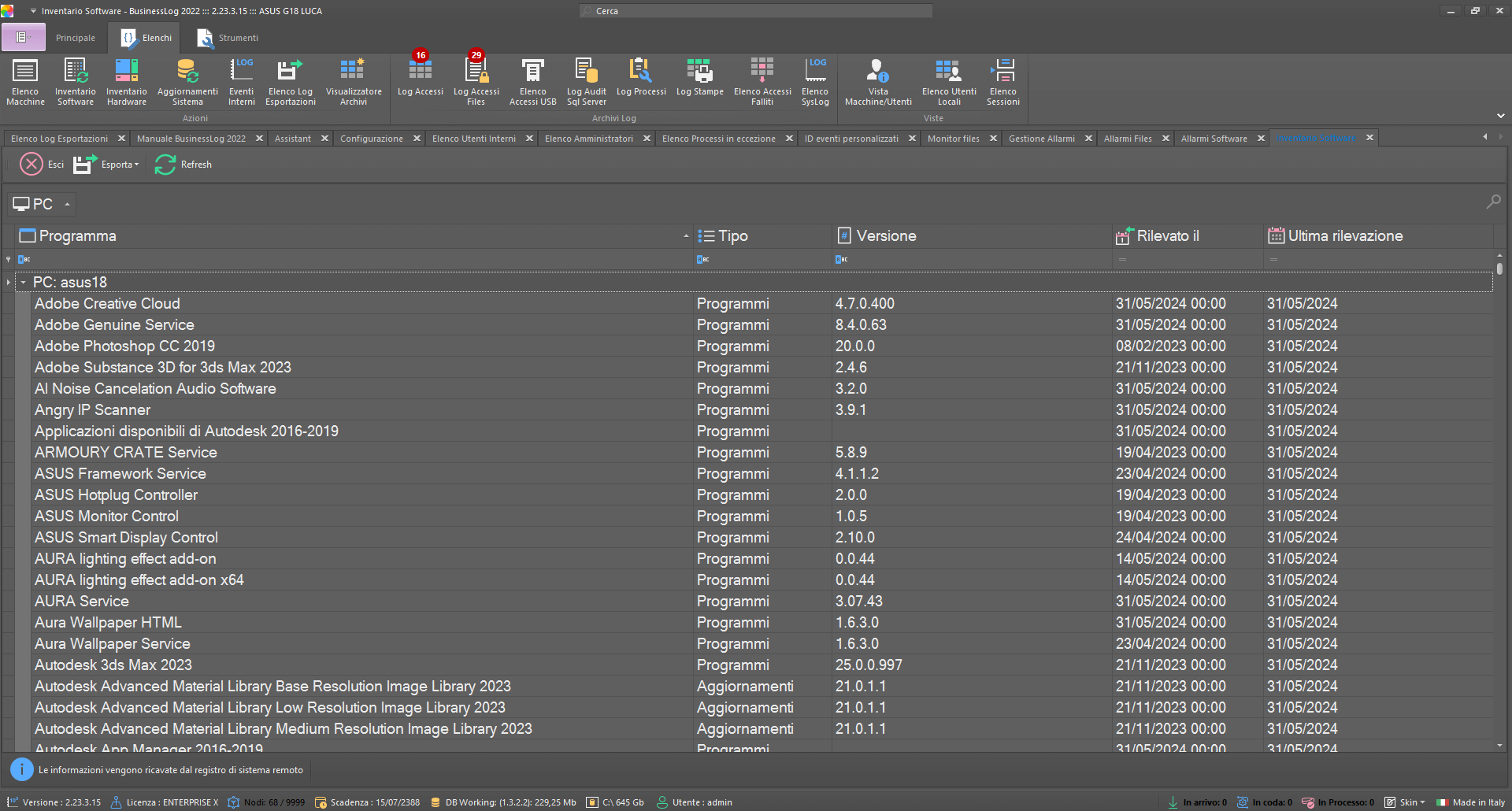
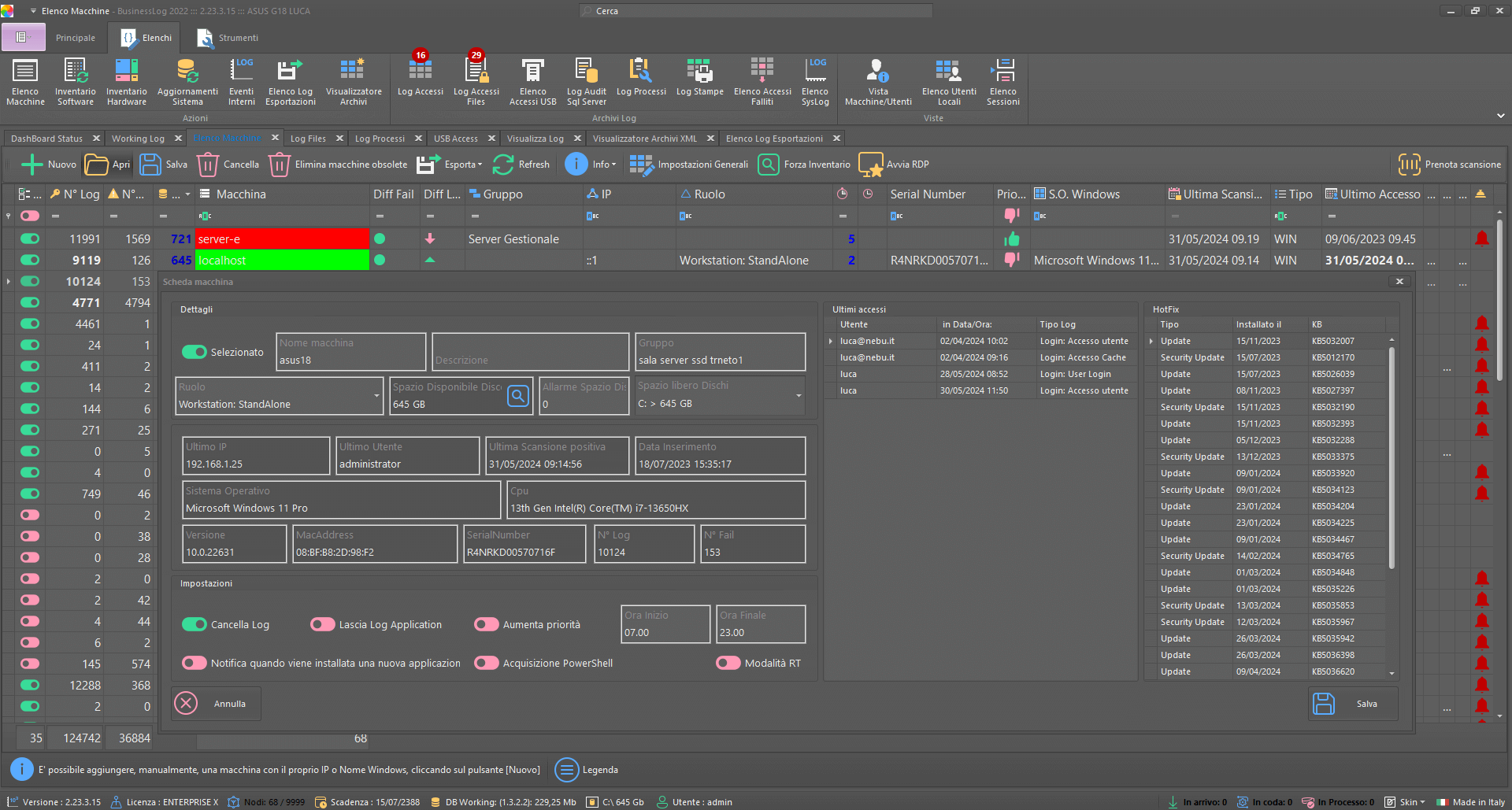
Automatic inventory
Business LOG automatically makes an inventory of the software and hardware in the organization's infrastructure.
Artificial Intelligence and Machine Learning
In the Registry Log, it is possible to query each individual Log in depth through Artificial Intelligence. The user will get a response (in understandable language) containing the nature and details of the log.
A dedicated Machine Learning performs, on a daily basis, training of the logs recorded in the archive to “learn” information related to user accesses.
Business LOG applies the model generated by the analysis to highlight anomalies in user accesses compared to the predictions of the Machine Learning generated model.
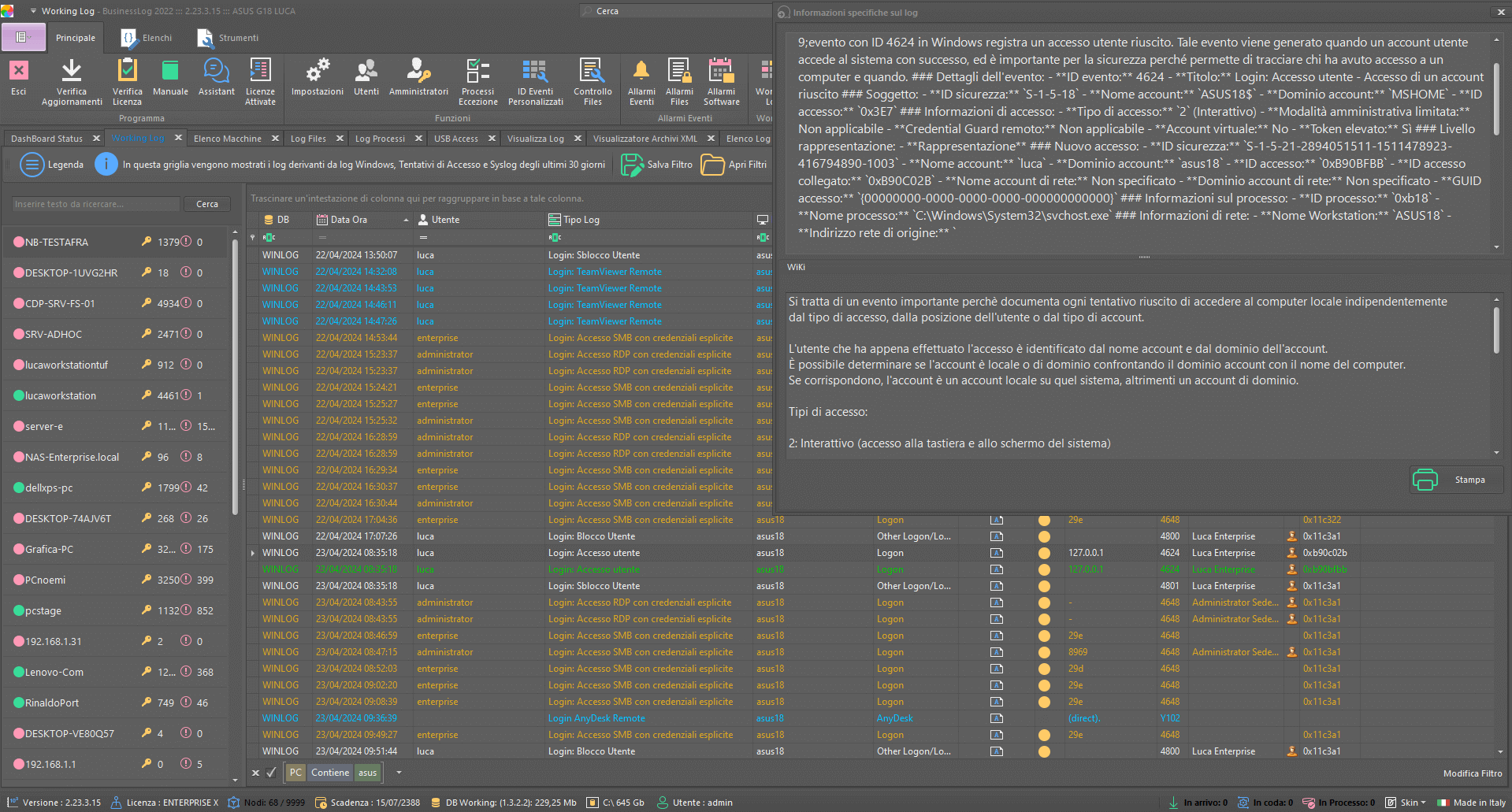
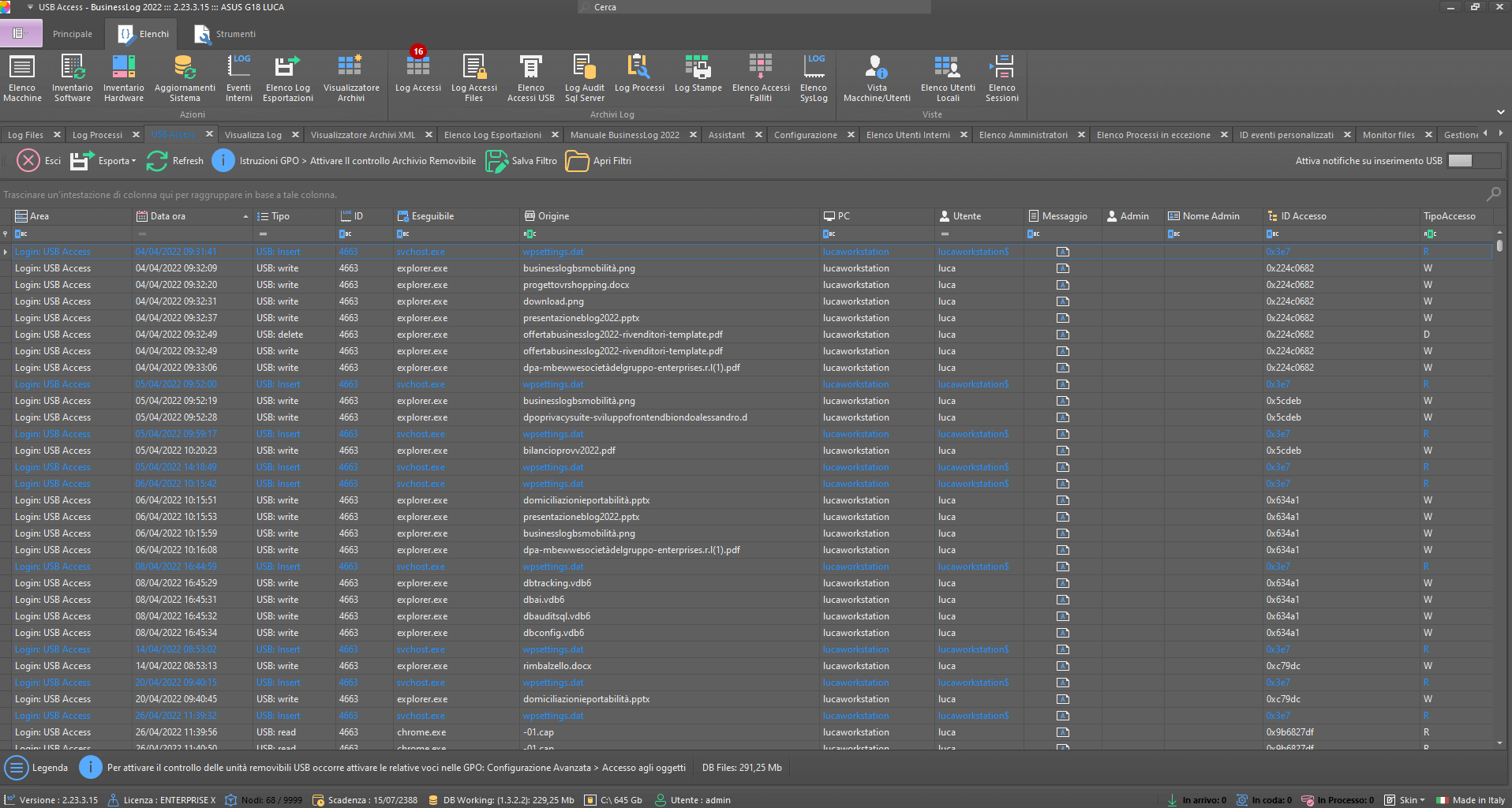
Log USB accesses
With Business LOG, access to USB devices and Removable Disks can be monitored to detect potential fraudulent activity and prevent errors or critical issues within the organization.
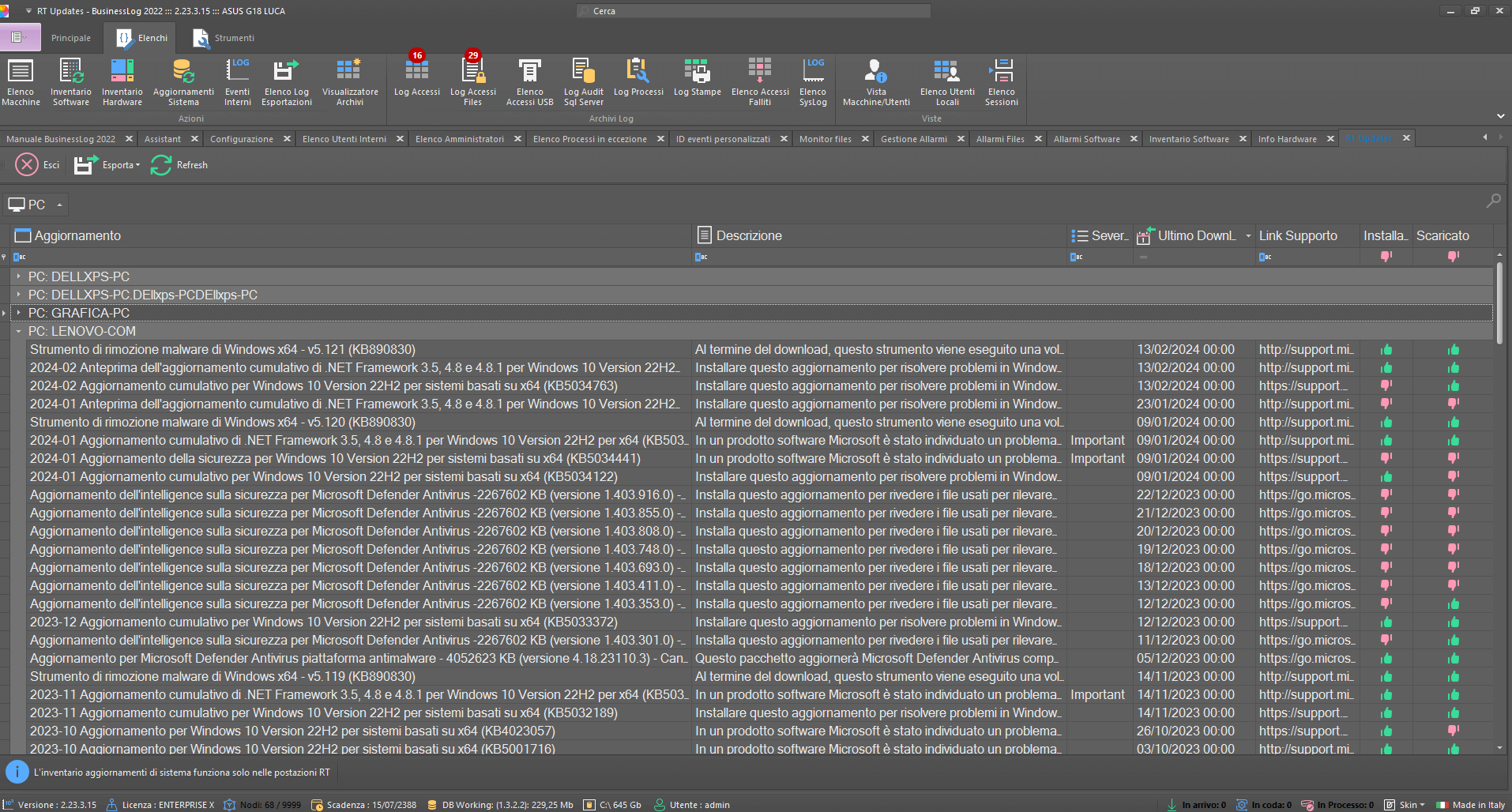
Windows updates
The controlled machines will receive, in a special list, all listed, downloaded and installed Windows Updates. In addition, all HotFixes applied will be written.
Discover Business LOG through its features.
Business LOG's Dashboard
Digitally signed logs
Event management
Activities on files
Syslog access logs
Process logs
SQL log audit
Advanced statistics
Telegram integration
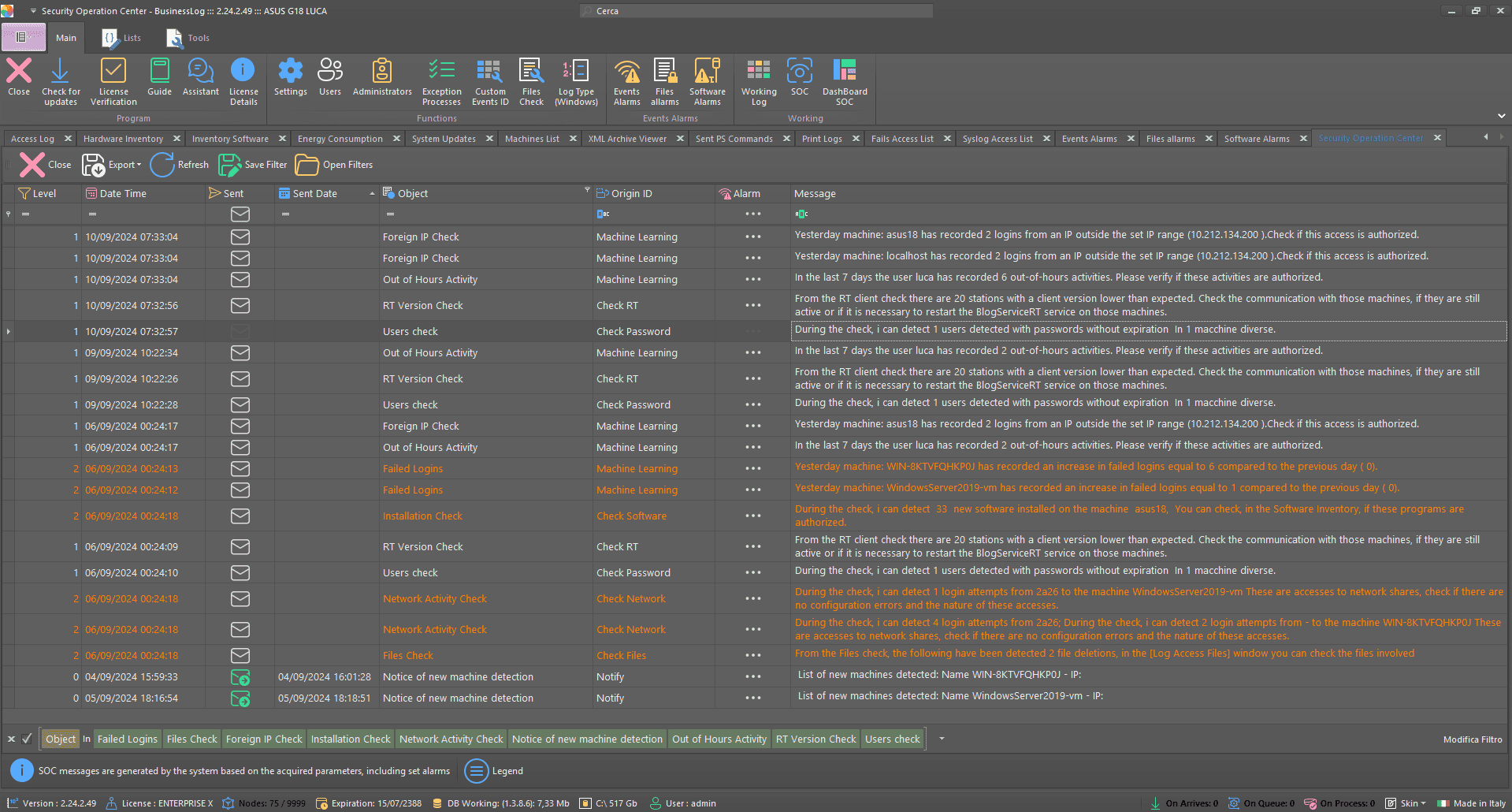
Business LOG SOC
Business LOG's Security Operations Center (SOC) function is designed to ensure the security and protection of corporate data. It provides continuous monitoring of network activities, identifying and responding to cyber threats in a timely manner. With Business LOG SOC, companies can rely on proactive surveillance and advanced defense measures to prevent attacks and ensure compliance with security regulations.
Real-time monitoring
Fast response to threats
Compliance with safety standards
Event Alerts with PowerShell
Reactive automation: when a selected event occurs, Business LOG uses an AI engine to generate and execute PowerShell commands in real time, following the rules set by the user.
PowerShell commands generated by AI
Real-time execution on selected events
Configurable rules and conditions

Machine Learning
Business LOG leverages the potential of Machine Learning to revolutionize enterprise log management. One of the main benefits of this technology is the ability to detect anomalies in user accesses by comparing them with the predictions of the learned model. This enables early identification of suspicious or noncompliant behavior, significantly improving the security of the company's IT infrastructure.
Detection of anomalies
Automation and efficiency
Continuous learning
Agentless, all features, full compliance.
Recommended for regulatory compliance only.
Cyber Security services
The growing importance of IT services and systems in business processes makes it necessary to pay greater attention to the systems themselves. Ensuring an adequate level of IT security is essential to protect the usability, integrity and confidentiality of data from increasing external threats. Learn about our services and how we can support your organization.
Request a Business LOG Quote
Are you interested in the Suite? Request a Business LOG quote now to evaluate the opportunity for your organization